Organizations use 40-plus products and IT tools on average to manage networks, SaaS applications, and endpoints. This fragmented approach creates data siloes and blind spots that hamper detection and incident response.
Attackers actively look for easy targets like misconfigured websites and unpatched applications to exploit. Service providers can leverage their strong business relationships and trusted advisor roles to help businesses protect their expanding attack surface and be more proactive regarding malware and breaches.
Expanding Attack Surfaces
An attack surface encompasses all the avenues that cyber criminals or unauthorized users can initiate an attack or extract data. Attack surfaces include networks, endpoints, cloud infrastructure, and SaaS applications. Digital transformation, work-from-anywhere, and always-on devices have expanded the attack vectors that defenders must safeguard.
Minimizing attack vectors to improve attack surface protection is not new. It’s a cybersecurity best practice in compliance frameworks such as the NIST Risk Management Framework (RMF).
Attack Surface Coverage Improves Business Security
 Author: Paula Rhea, product marketing manager, Netsurion
Author: Paula Rhea, product marketing manager, NetsurionBusinesses have many points of vulnerability, too many to monitor and protect on their own. Executives may not be aware or prepared for today’s sophisticated threats. IT decision makers may be so focused on daily operations and putting out fires that they overlook tool sprawl that limits visibility and actual cybersecurity effectiveness.
Some benefits of attack surface coverage include:
- Enhance security coverage no matter wherever data resides
- Unified view of risk with comprehensive visibility
- Faster detection of threats and malicious activity
- Additional cost savings when infrastructure and security is optimized
Service providers are well-positioned to defend against financially motivated attackers looking for easy business targets.
Best Practices to Minimize Attack Surface Risk
Reduce the potential for a successful attack with these practical steps:
Step 1: Identify and shore up any vulnerability gaps
Layered security defenses are needed to quickly mitigate threats posed by persistent and well-funded adversaries. The first tactic used by cyber criminals is network reconnaissance which looks for unpatched vulnerabilities and configuration errors. Think like a hacker to help your clients shrink their attack surface with rigorous scanning, vulnerability management, and guided remediation steps.
Step 2: Boost endpoint protection where attackers often enter
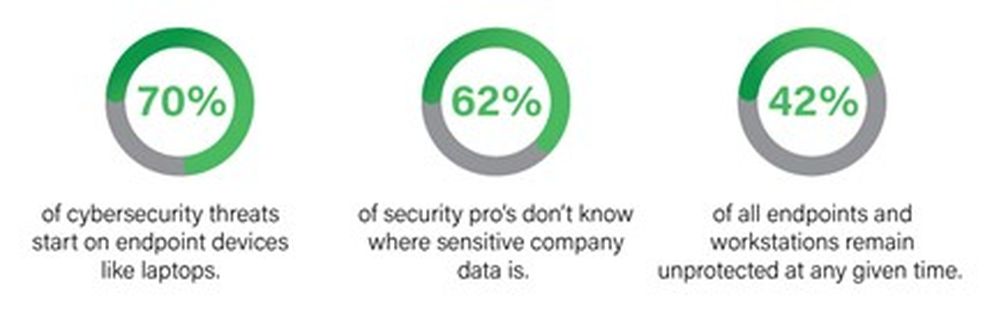
Endpoint security is vital as 70% of data breaches occur via compromised laptops and workstations. Coverage gaps and the lack of insight into where critical data resides hamper device security.
Service providers can use a prevention-first approach followed by detection and response against known and unknown threats to minimize attacker exploits on business endpoints.
Step 3: Simplify tech stack complexity
The explosion in point products and tools leads to integration blind spots, underutilized investments, and alert fatigue trying to swivel between them all. Eliminating unused or default functionality and redundant products can reduce attack surfaces and risks. Streamline and simplify your infrastructure with solutions like extended detection and response (XDR) that offer improved visibility and the ability to “connect the dots” for faster threat detection and response.
Step 4: Increase cloud security for comprehensive protection
Software-as-a-Service (SaaS) applications and public cloud infrastructures like Amazon Web Services (AWS), Microsoft Azure, and Microsoft 365 (M365) are mission critical. The widespread adoption of cloud computing and shortage of cloud security expertise make cloud security even more essential.
Cyber criminals know that cloud attack surfaces are often overlooked and misconfigured. Holistic attack surface coverage that includes cloud security can alert you to cloud security gaps and guided remediation steps long before a disastrous failure occurs.
Step 5: Implement network segmentation
Break the network up into logical groups with separate security policies and access. The goal of micro-segmentation is to limit the impact of any unforeseen data incident and make it more difficult to move laterally across an organization. While not new, network segmentation is a relatively easy way to protect infrastructure and attack surface.
Step 6: Enhance visibility and event correlation
One crucial way to improve visibility is to unify logs and device telemetry for a single source of truth. Log integration across firewalls, applications, databases, and cloud infrastructures enable service providers to respond rapidly to security incidents at scale.
Look for vendor-neutral partners that leverage existing infrastructure, security licenses, and telemetry out of the box. This open approach provides greater visibility and avoids rip-and-replace projects. Cybersecurity experts in a 24/7 security operations center (SOC) then augment technology to provide guided remediation steps that simplify service provider operations.
Netsurion Brings it all Together
In a connected and always-on world, ignoring security gaps jeopardizes networks and business resiliency. Safeguarding IT infrastructure and sensitive data is challenging and requires constant vigilance and 24/7/365 monitoring. A managed solution augments IT teams and decreases false positives, a boon to overworked MSPs and cyber defenders.
Learn how Netsurion’s Managed Open XDR covers the entire attack surface across endpoints, servers, SaaS applications, and cloud infrastructure.
Author Paula Rhea is product marketing manager for Netsurion. Read more Netsurion guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




