Threat hunting is gaining traction as businesses look for more proactive methods to combat multi-stage ransomware attacks and devious “low and slow” hackers. Threat hunting complements threat detection and response to provide a more comprehensive and layered approach. Many managed service providers (MSPs) actively seek ways to become proactive and offer guided remediation that actively stops and blocks threats. The lack of staff and skills, along with unfamiliarity with threat hunting processes and techniques, can all inhibit adoption.
With a better understanding of what truly is threat hunting and identifying common misconceptions of threat hunting, you’ll be set to successfully add it to your cybersecurity services portfolio.
What is Threat Hunting
Threat hunting can uncover threats you might otherwise not discover until a data breach is found, often months later. Threat hunting is the process of proactively and iteratively searching to detect and isolate advanced threats that evade existing security solutions. This proactive defense creates a rapid response before attackers change their methods or escape detection.
Threat Hunting Advantages
In addition to reducing risk, proactive threat hunting offers benefits to MSPs and their end-customers. These advantages include the ability to:
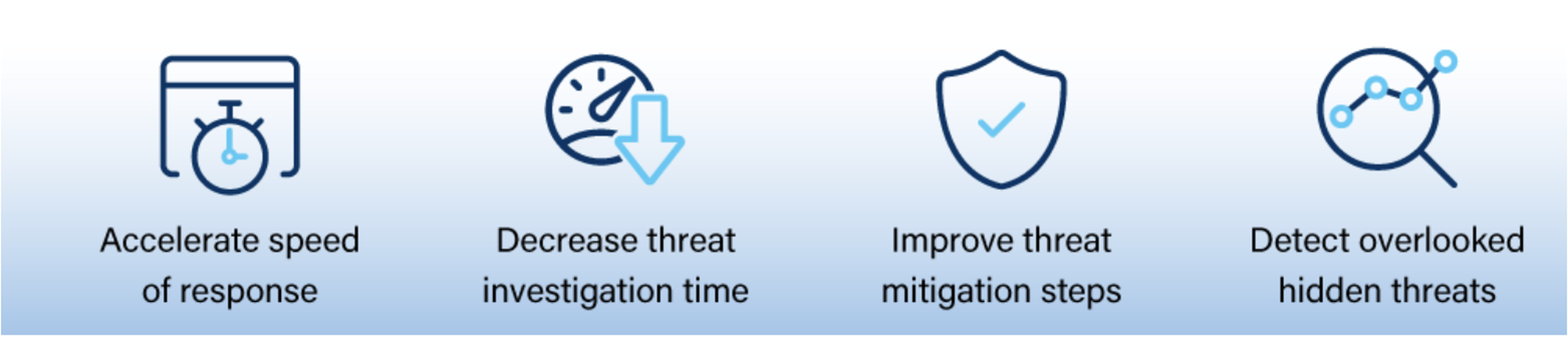
MSPs should also serve as cybersecurity role models to implement threat hunting for early threat detection and cyber resilience in their organizations.
Misconceptions About Threat Hunting
Here are some real-world insights from Netsurion Security Operations Center (SOC) analysts to separate threat hunting myths from reality:
Myth # 1: Threat hunting can be fully automated. Artificial Intelligence (AI) is all the rage, and companies are in overdrive to exploit the term. The reality is that the analytical nature of the threat hunting process prevents it from being fully automated. Humans will always be needed as part of the cybersecurity process to identify cyber criminals who mutate their tactics, techniques, and procedures (TTPs) to evade automated detection. However, the data collection and threat context enrichment steps can often be enhanced and accelerated with automation.
Myth # 2: Anyone can hunt. The best hunters are curious and passionate people who understand the ever-changing threat landscape. They use this expertise to tailor threat hunting for customer environments, industries, and risks. Indeed, formulating the correct question is the critical first step for cyber analysts in hunting. It also involves looking for suspicious behavior that automated tools alone won’t uncover. Most organizations lack threat hunting proficiency, so Netsurion includes threat hunting as an integral capability of its managed solution.
Myth # 3: Threat hunting is the same as penetration testing. These two security practices have different objectives. A penetration test is an authorized attempt to hack and gain access to an organization's data assets while acting as a malicious external actor. Its purpose is to identify exploits for a rapid threat response before any potential cyber attack. On the other hand, human-led threat hunting identifies threats (potential or ongoing) that penetration tests may not have picked up internally.
Myth # 4: Threat hunting always finds malware or attackers. More often than not, threat hunting will find more policy violations and misconfiguration than any malware or cyber criminals. Such detections are highly valuable and actionable, and addressing them reduces noise. Eventually, though, threat hunting will uncover evil.
Myth # 5: Threat hunters spend most of their time hunting. Surprise! A lot of a threat hunter’s time isn’t spent threat hunting but preparing the hunt plan. These steps can include research and testing as well as approvals, developing documentation, or educating network owners that adding a new log source is truly necessary. Post-hunt tasks include documenting results, presenting findings, and building threat detection content and playbooks for the SOC. A hunter spends less time in an actual threat hunt and more time preparing before and after the real threat hunt itself.
A Way Forward
MSSPs are seeing an uptick in demand for threat hunting by their customers. The rise in ransomware and public scrutiny regarding cybersecurity incidents has fostered a need for proactive adversary detection and response. As you explore ways to offer threat hunting to your customer base, look for master managed security service providers who build these hunt capabilities into their solutions to do the heavy-lifting behind the scenes. Netsurion Managed Threat Protection predicts, prevents, detects, and responds to advanced threats to stay ahead of cyber criminals when every minute matters.
Author A.N. Ananth is chief strategy officer at Netsurion. Read more Netsurion guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




