Have you noticed that people are just too busy to read important information you send to them? One of the problems with disseminating information, especially when it is about cybersecurity, is that there needs to be a balance between timing, priority, and cadence.
Timing is simply when the message is sent.
You may send a message of the utmost urgency, such as a warning about a ransomware outbreak. However, if you sent that message at 3AM, it will probably be ignored amidst all the other E-mails that arrived overnight in the recipient’s in box.
Priority is the importance of the message.
Yes, you can flag a message as high importance, or some similar setting in your mail client, however, your priorities are not necessarily the same as the recipients’, so your important message may not generate any heightened interest.
Cadence is the frequency of your messages.
Do you send too many messages? If you do, you run the risk of the “boy who cried wolf” problem, where people will just ignore most, if not all, of your messages.
What can you do to get someone to read the message, or at least retain the most important part of the message? Sure, you could write a single line message, but that would offer no context.
I recently ran into a problem when I needed to send a message warning of a voicemail phishing scam. I needed high engagement, yet I had previously sent another message about another security event, so my cadence was too tight, and my frequency too close. How could I engage the recipients to notice this message above the other?
One interesting technique of social engineers is to use misinformation, or concession. This technique, as well as many others, is explained beautifully in Chris Hadnagy’s book “Social Engineering – the Science of Human Hacking”.
Here is how I used it to grab the readers’ attention. First, I sent the message that many people may not have entirely focused on:
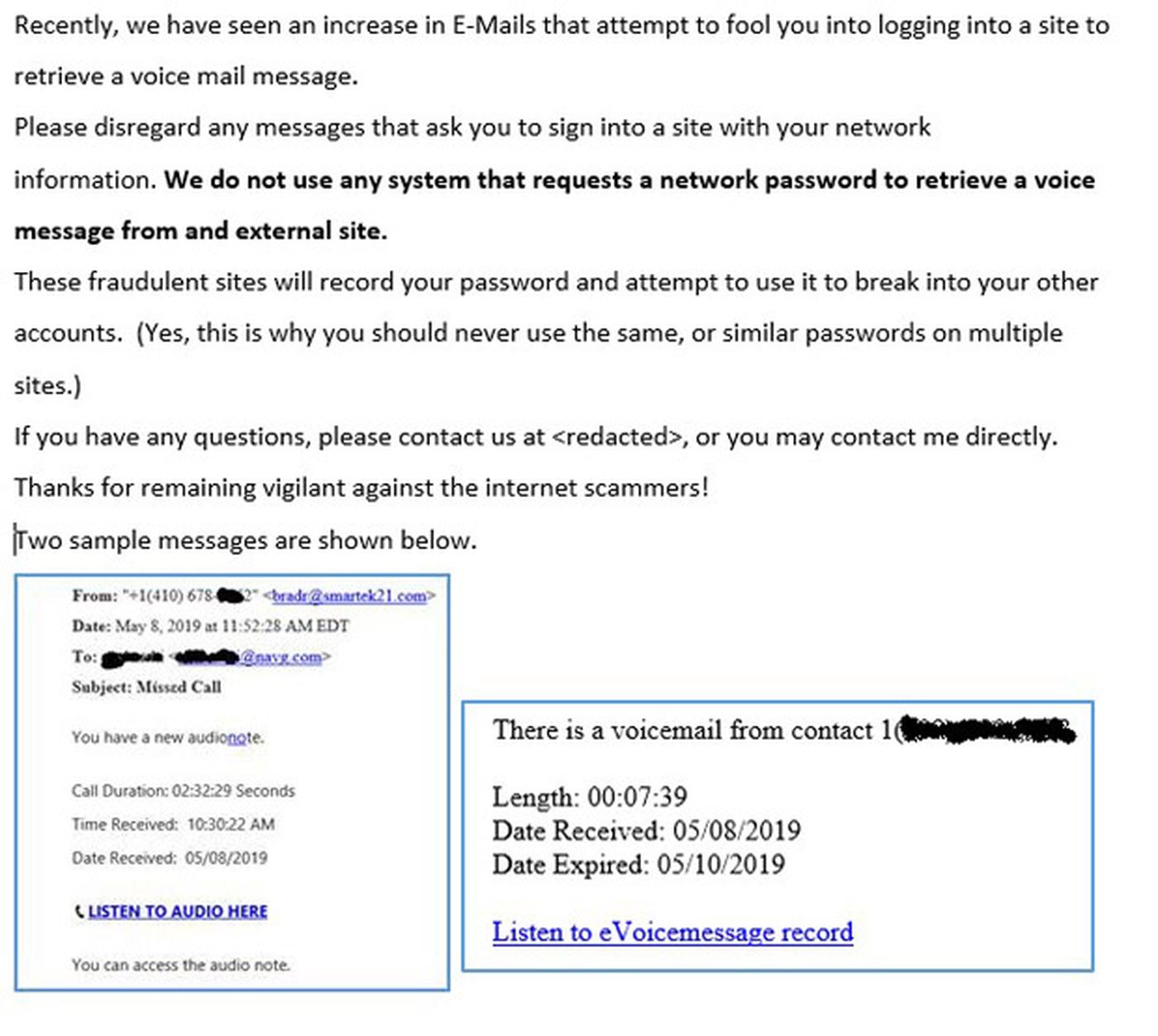
If you are a total grammar, (or typo) geek, you may notice the error I made in the sentence:
We do not use any system that requests a network password to retrieve a voice message from and external site.
Once this message settled in, (or became buried beneath the recipients’ other priorities), I followed it with this message:

Using this deliberate error, and conceding to the error, the reader is not only drawn to the most important idea in the message, but the reader may actually go back to look more closely at the original message, which offers a better chance of the recipient internalizing the message.
Of course, the nature of this technique could be perceived as manipulative, however, no one was harmed through its use. Also, it certainly cannot be used too often. Like all good tools, its effectiveness becomes dulled with overuse. Again, this is also part of the balance of social engineering skills, and if you have not already read Chris Hadnagy’s book, it is highly recommended. He can teach you how to use, yet not abuse, some of the best techniques in the social engineering profession to excellent effect.
If used judiciously, concession is a powerful tool to engage a population suffering from information-overload. Tread lightly!
Author Bob Covello (@BobCovello) is a 20-year technology veteran and InfoSec analyst with a passion for security topics. Blog courtesy of AT&T Cybersecurity.