
Each MSSP offers a unique set of services to their customer base with differentiation and operational efficiency frequently among top management priorities. Selecting the technical components to formulate service offerings around is perhaps one of the most important decisions MSSPs need to make. MSSPs reading this are strongly encouraged to consider adding Wi-Fi security products focused at detecting and preventing the six Layer Two Wi-Fi threat categories that nearly every business has been vulnerable to for the last twenty one years.
The Twenty-one-year Problem of Wi-Fi Security is deep within the protocol and can be summarized in the below illustration. Any attacker with something like a Wi-Fi pineapple and YouTube can broadcast the same SSID as a business (a bank for example) and endpoints will auto-join this evil twin access point allowing the attacker full man-in-the-middle (MitM) position to intercept anything the victims access over Wi-Fi.
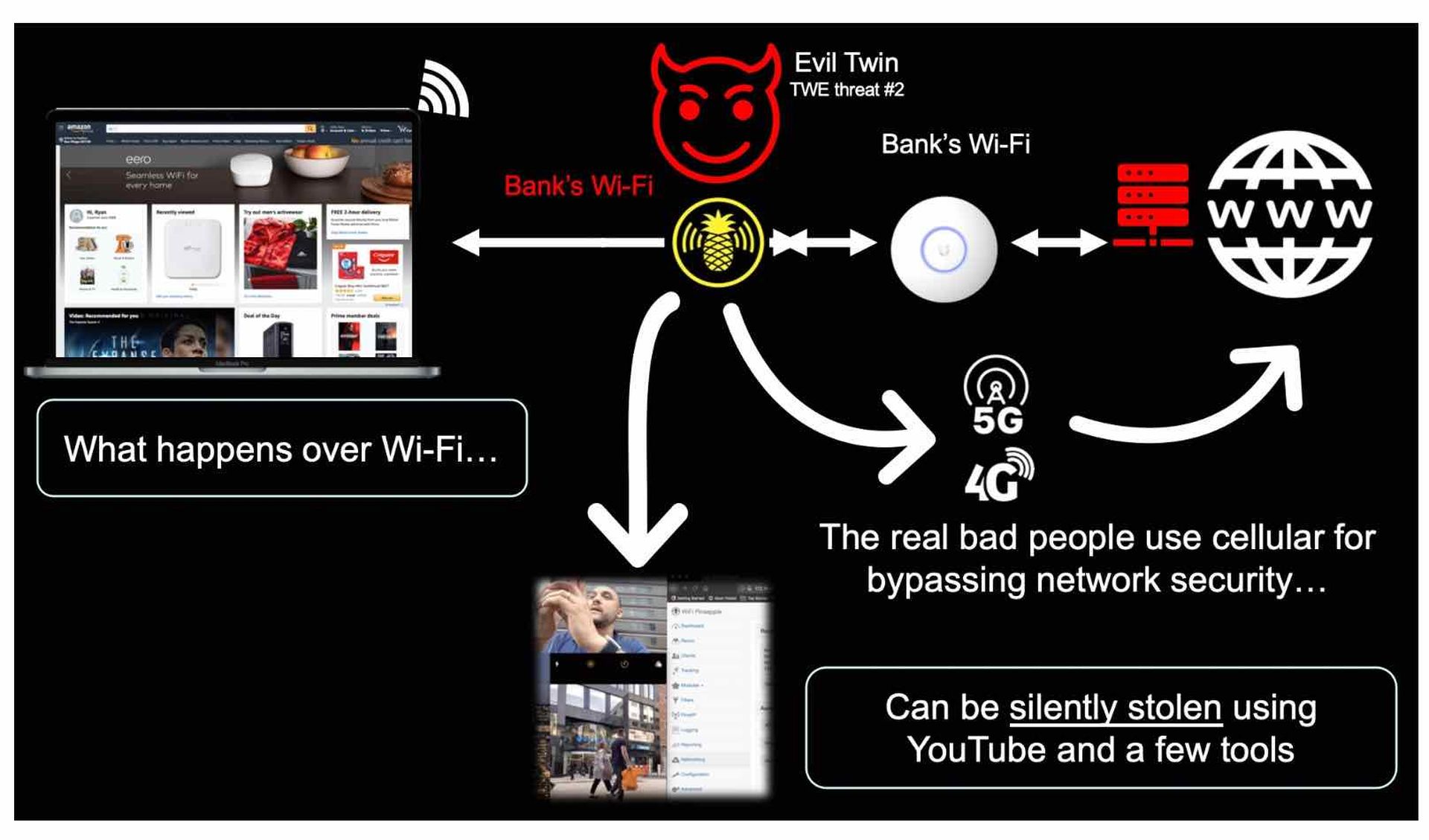
The Opportunity for MSSPs is to add to their stack an access point (AP) vendor with Wireless Intrusion Prevention System (WIPS) software running inside them that can automatically detect and prevent the six Wi-Fi threat categories (the evil twin is threat #2). WIPS is not an industry standard however, so be sure to research if the brand of APs your customer has or you wish to include in your MSSP stack has been independently verified to automatically detect and prevent the six wi-fi threat categories. WIPS features and functionality vary widely by AP vendor. Some AP vendors allow their APs to be configured as dedicated WIPS security sensors which allows customers of MSSPs to keep their existing APs installed and simply add WIPS sensors into the network for securing the air space. The number of WIPS sensors needed varies by physical environment but a general rule is one WIPS sensor for every three to four APs.
If we review common components in most MSSPs stacks, we’ll see where Wi-Fi security fits in:
- Network and Device Security Components include products like firewalls, SD-WAN security gateways, and endpoint prevention software such as antivirus/malware/etc. These products are aimed mostly at securing north-south communication and threats targeting individual devices with fairly well-known attacks. This is the area that Layer Two Wi-Fi security products fit into.
- Security Information and Event Management (SIEM) software tools are the keystone for a MSSPs operations aggregating event information from network, endpoint, Cloud to identify security risks and vulnerabilities. When adding Wi-Fi security into your stack, look for AP vendors that allow exporting log files automatically such as a syslog stream to be digested by your SIEM.
- Endpoint Detection and Response (EDR) software goes beyond traditional antivirus looking for anomalous behavior and patterns. When selecting your AP vendor with WIPS capabilities, make sure the vendor can support identifying the fourth Wi-Fi threat category: rogue clients, which are endpoints that have been detected to have connected to a rogue AP and may have malware loaded.
- Vulnerability Assessment (VA) tools are typically looking holistically at networks, endpoints, and Cloud applications for best practices, known software version vulnerabilities, and various regulartory compliances. In your search for an AP vendor with WIPS, make sure they support reporting and testing for Wi-Fi security vulnerability assessments and testing for compliance with common regulations such as PCI DSS, Sarbanes-Oxley, and HIPAA.
Also emerging in more MSSPs stacks are the below components highlighting where Wi-Fi security fits in:
- Cloud Access Security Broker (CASB) tools range in functionality and allow MSSPs to monitor their customers’ Cloud app usage, detect if personally identifiable information (PII) has accidently been transferred to a Cloud app, and if any malicious files accidentally went into various Cloud apps among other features. Although MSSPs have several tools to limit or block various Cloud applications being used on their customers’ networks, look for APs with WIPS that can prevent threat number 3, the neighbor AP, which allows employees to bypass web content and application controls by tethering their devices to mobile 4G/5G hotspots or nearby guest Wi-Fi.
- Security Automation, Orchestration, and Response (SOAR) tools automate tasks for MSSPs and you should look for AP vendors with WIPS alerting features that allow the SOAR platform to digest Wi-Fi security events and respond automatically.
Adding Wi-Fi security into the stack is an incredibly rewarding offering for MSSPs and their customers. As with any stack component decision, do the research and ask the AP vendor or search online for test reports to determine if their APs with WIPS can automatically detect and prevent the six know Wi-Fi threat categories. This is a key advice to MSSPs who understand that a stack component needs to be easy to quote, deploy, manage, and automate. For more educational information on Wi-Fi hacking and security see TrustedWirelessEnvironment.com.
Ryan Orsi is director of product management at WatchGuard, where he leads the Secure Wi-Fi solutions for the company. Read more WatchGuard guest blogs here.




