At RSA 2019, we conducted a survey that netted 733 respondents along with interviews between Javvad Malik, former security advocate at AT&T Cybersecurity, and security experts. The full results are in his comprehensive and informative research report. Following are a few highlights:
Internal Threats
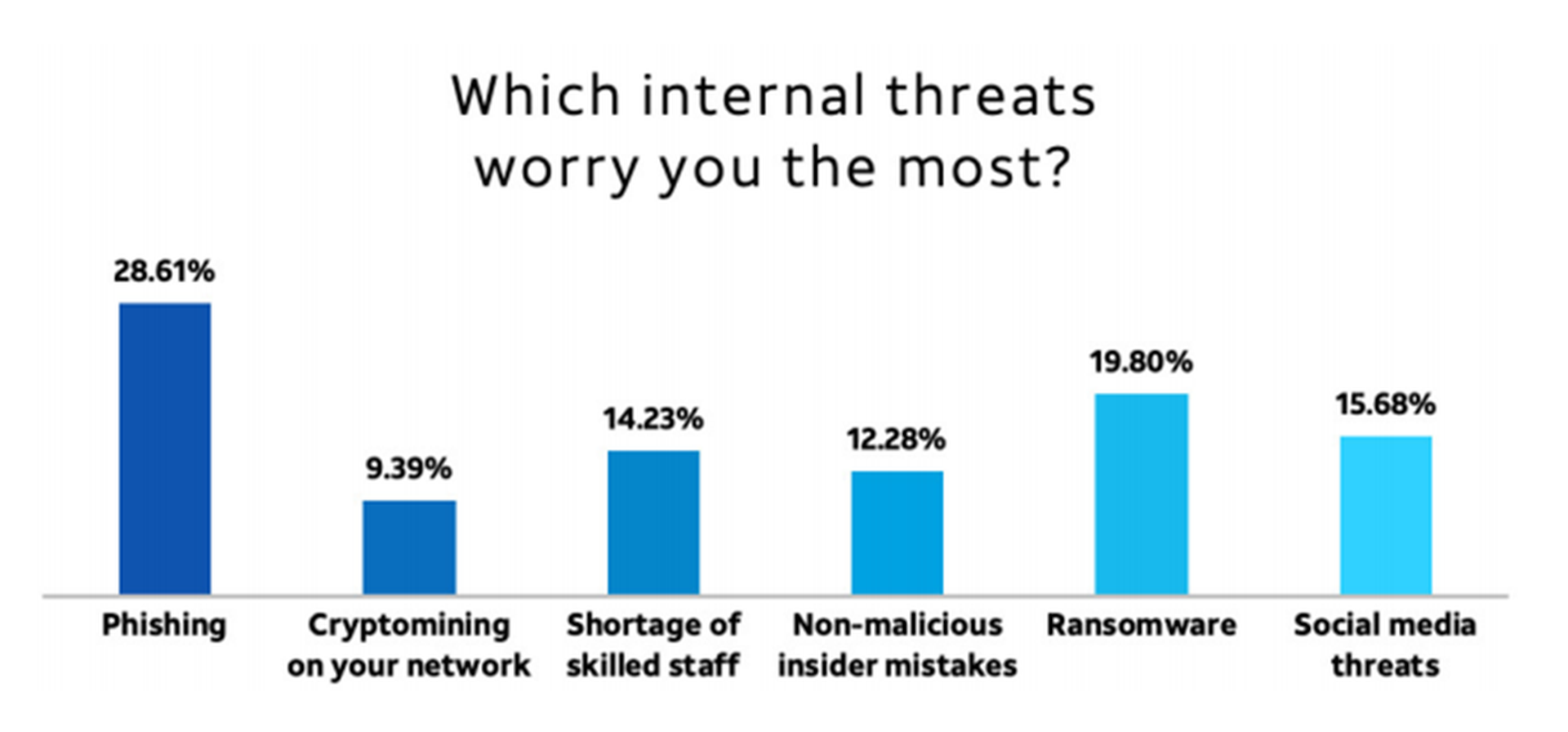
Phishing is the clear “winner” here. At 29%, nearly a third cited phishing as the threat that worries them the most. Phishing comes in different guises for different purposes. Sometimes phishing emails are used to deliver a malicious payload. Other times it’s to social engineer the recipient by gaining their trust or scaring them by posing as an authority to get them to make payments—as we often see in business email compromise (BEC) attacks. Ultimately, this likely boils down to the fact that for most cyber threats, a technology solution is usually available to ward off attacks, but with phishing, most systems rely heavily on the email recipient being able to detect and respond appropriately.
In second place comes ransomware, which has entered into the vocabulary of nearly everyone in the last few years. The biggest challenge with ransomware is that, unlike other attacks, there is no hiding from the fact that systems have been compromised; and even if recovery is quick and without any loss of data, the reputational damage can be detrimental.
Social media threats showed up in third place, with 16% of participants citing it as a worry. This, perhaps surprisingly, is ahead of having a shortage of skilled staff. Delving into this, though, it makes perfect sense. Social media has rapidly become an unmanaged and uncharted source of risk for many companies. Any mistake can impact brand and trust, expose sensitive information, or indeed become a source of entry into an organization.
External Threats
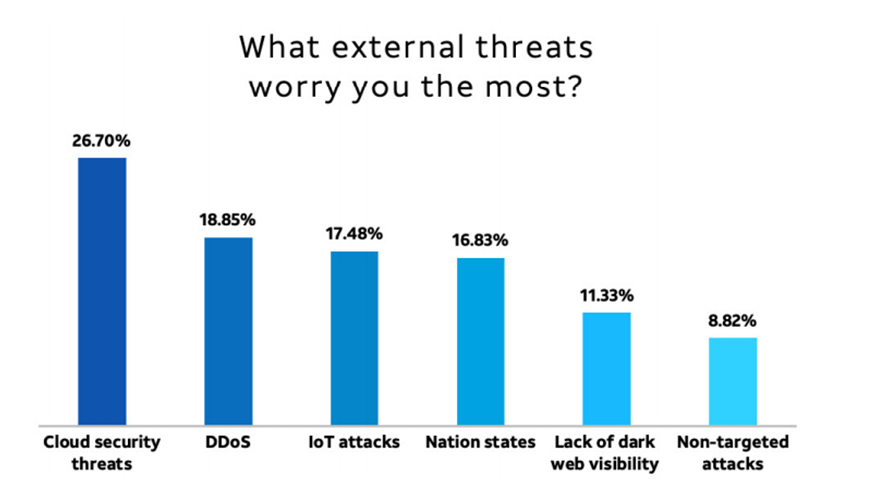
When asked the same question about external threats, cloud security threats were cited as top worry in 27% of all responses. While it may feel as if discussions around cloud and cloud security have been ongoing for many years, it is still a relatively new area for many companies. The implications of moving to the cloud with or without a well-defined strategy are being felt today, and with so many data leaks attributed to misconfigured cloud databases, or through poor credential management, companies are right to be worried.
Distributed denial of service (DDoS) attacks were in second place, closely followed by Internet of Things (IoT) attacks and nation states.
The rest of the story
The learn more details on the survey methodology, how well InfoSec pros and execs see eye-to-eye, results broken down by industry sector and company size, plus the conclusions we can draw, please read the research report. The whole report is available on our website, in the Resource Center.
Kate Brew is editor of the AT&T Cybersecurity blog. Read more AT&T Cybersecurity blogs here.




