

You’d think that as more organizations engage MSSPs to develop security architectures, the road map to maximize those engagements (and relationships) would be pretty straightforward by now. Turns out, maybe not so much.
What do customers want from their MSSPs? What are the keys to successfully shaping an MSSP engagement? Researcher Gartner has updated its “How to Work With an MSSP to Improve Security” to help customers and MSSPs chart the waters. This latest edition includes a new guidance framework (more on that in a minute).
There are a great deal of details, explanations and things of that nature in the report (you can have it for a fee). But the one message that supersedes all the minutiae: Work together. “You must work with the MSSP, not expect them to figure everything out alone,” wrote Augusto Barros, Gartner research director and co-author of the report, in a blog post.
Both Barros and co-author Anton Chuvakin, a Garter distinguished analyst, lay out a case that for organizations and MSSPs the time is now.
“It’s very common to start a call about SIEM, UEBA, NTA or EDR and end it talking about MSS, after the client realizes that using those tools require people – a lot of people – on their side,” said Barros. The report also cautions organizations expecting to be hands-off once they hire an MSSP to oversee the security monitoring process:
“When customers perform triage, they will often find cases of false positives,” he said. “Many organizations don’t report these back to the MSSP, only to complain later that they keep receiving the same false-positive alerts repeatedly! Although the MSSP is responsible for tuning the detection systems it manages, such tuning typically requires feedback from the customer.”
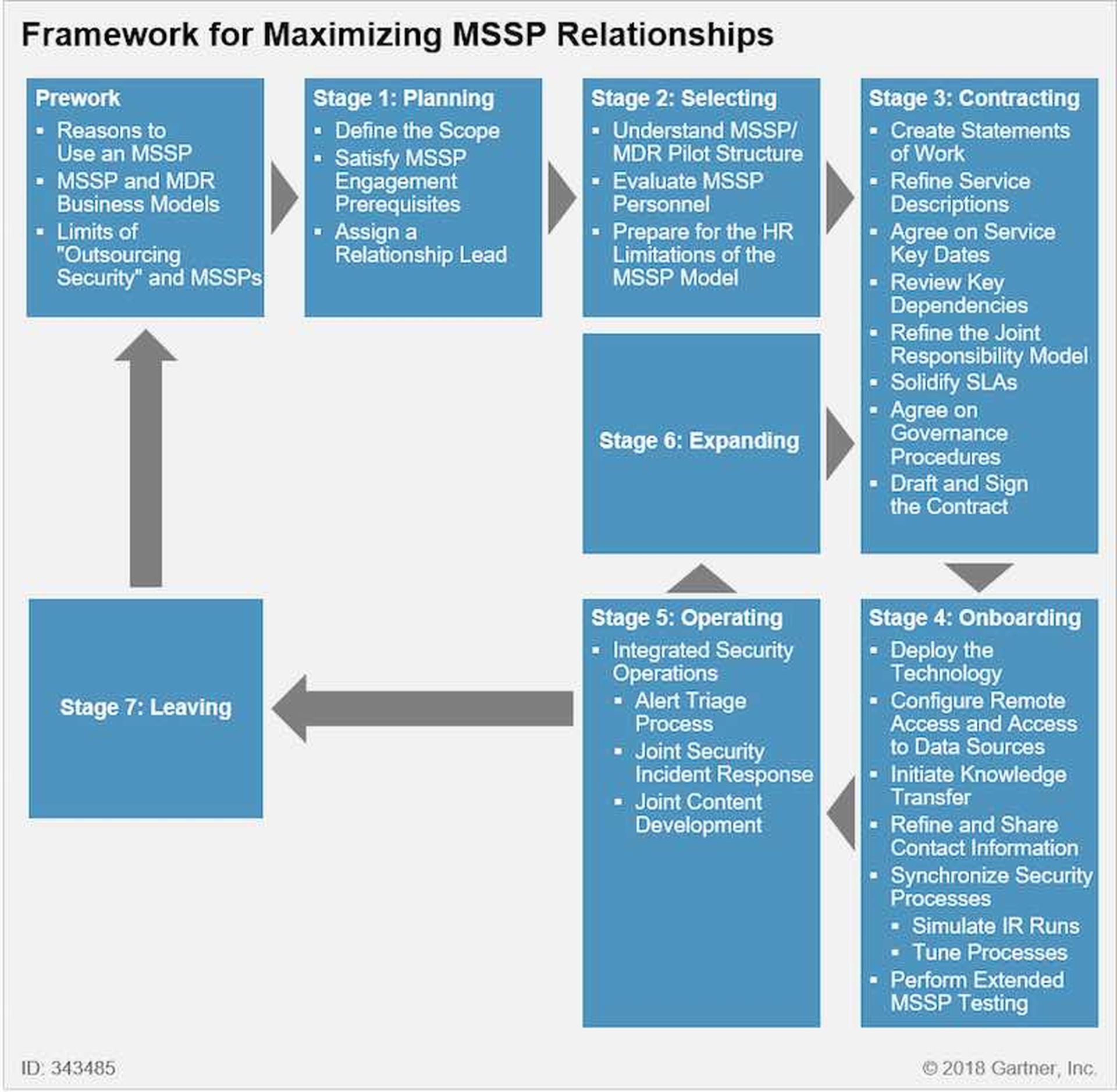
Here is Gartner's seven-stage framework of an MSSP engagement for customers (and providers) to digest (abridged):
- Prework: List your reasons for working with an MSSP.
- Stage 1: Planning. Define the scope of work; assign a lead.
- Stage 2: Selecting. Evaluate MSSP personnel.
- Stage 3: Contracting. Create statements of work; solidify SLAs.
- Stage 4: Onboarding. Deploy the technology.
- Stage 5: Operating. Integrated security operations.
- Stage 6: Expanding.
- Stage 7: Leaving.
(Note: Check out the graphic below for expanded explanations of stages 1 - 5).
Chuvakin has pulled a few notable quotes from the report, which may give you a feel for its contents (abbreviated here):
“Using an MSSP is not the same as shifting responsibility for your security to somebody else. It involves integrating with an external security monitoring and system management paradigm, often using the provider’s standardized processes.”
“Organizations that have not retained sufficient internal IR and remediation capabilities cannot benefit fully from either MSSP security monitoring or an MDR-level version.”
“MSSPs can only work with the information you give them. ”
“In almost all cases, the organization will need to define and allocate some program management resources to keep the MSSP on task and evaluate its ongoing effectiveness."
“Failure to detect does not necessarily equal incompetence. For example, a failed detection is only an MSSP failure if the MSSP was given access to the necessary log data. If the MSSP didn’t have such access, the real question is, “Why not?”
“Sadly, some relationships come to an end, and your relationship with an MSSP may need to be one of these.”
Guidelines for what customers should expect in an MSSP engagement have been done before. A noteworthy example is a 2013 SiliconAngle piece, re-purposed three years later in a Forsythe Focus discussion outlining seven key steps to a successful partnership with an MSSP.




