The English poet John Donne famously opined that "no man is an island entire of itself." We might say the same for today's businesses operating in the globalized, information-rich economy.
For every company offering a service or product to customers, there may be hundreds of others behind the curtain helping to facilitate that transaction's journey: manufacturers and engineering firms, distributors and resellers, licensed service providers and software vendors, plus subcontractors, brokers and more.
Managed security service providers (MSSPs) need to be aware that if their clients enter relationships with third- or fourth-party vendors, it puts those clients at greater risk of data breaches and other forms of cyberattack. A troubling correlation has emerged: The more third parties an organization depends on, the higher the frequency of breaches and data leaks.
This doesn't mean that companies should scale down the number third-party relationships to mitigate the risk. Rather, the goal is for organizations and their MSSPs to understand the risks associated with managing third parties and to take steps toward lessening the risks.
Managing risks: What the data confirms
In late 2022, CyberRisk Alliance Business Intelligence surveyed IT security leaders, administrators and compliance professionals to understand their concerns and strategies for addressing third-party risks. According to the data, several factors are responsible for exacerbating these risks in recent years.
More third parties = greater complexity
It's the nature of doing business: One company (let's call it "A") finds that another company ("B") can provide a service or value at less expense than it costs A to do it. Thus, a business relationship is formed.
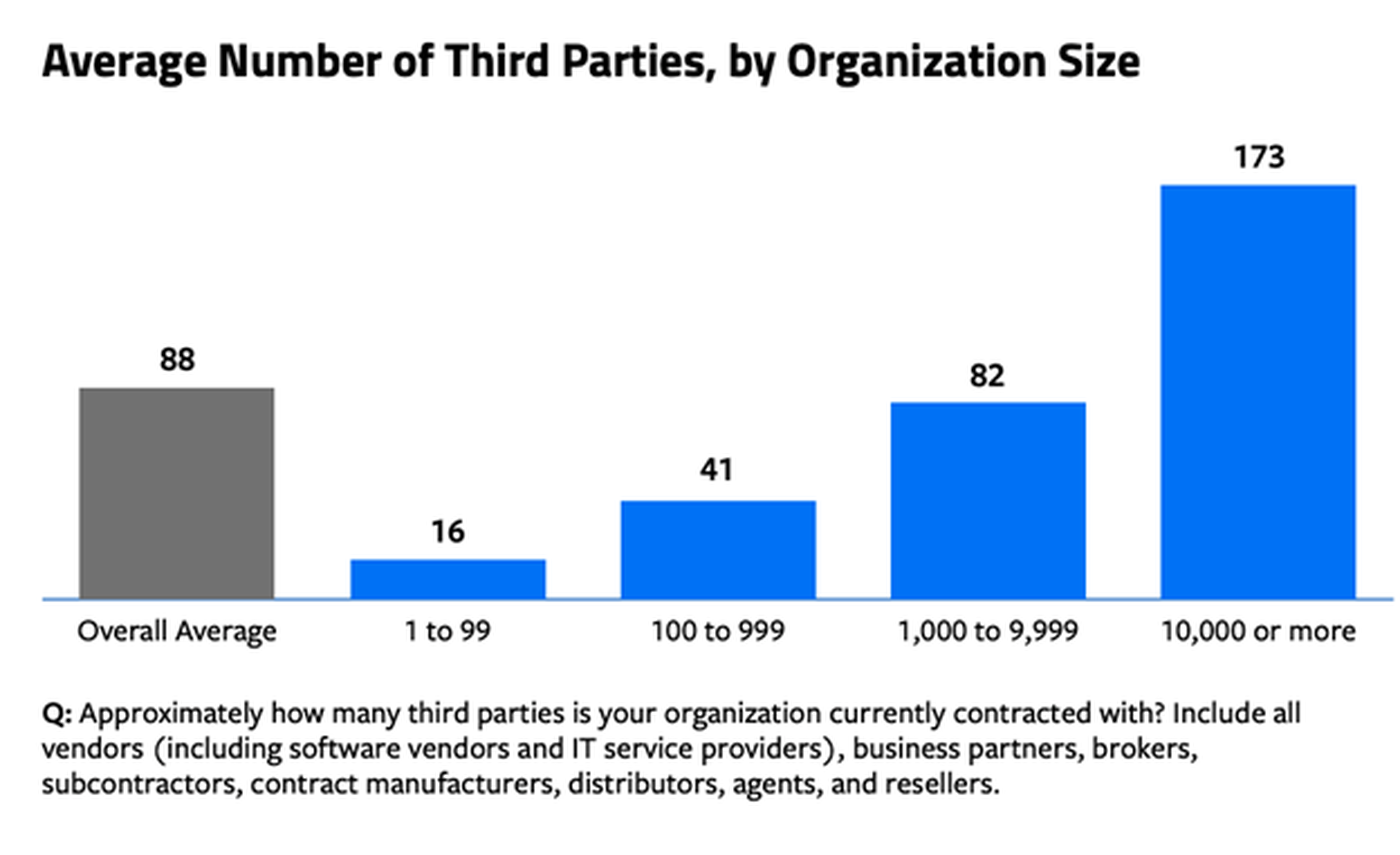
These sorts of relationships become more common as businesses scale and diversify their services to reach more customers. According to the CRA survey data, the average estimated number of third-party partners among all respondents was 88. In large enterprises of 10,000 or more employees, however, that number rose to 173.
When asked about why they used so many third-party vendors, respondents pointed to several factors: the COVID-19 pandemic and the resulting spike in remote work, the expansion of SaaS and cloud services, and increased pressure from customers, insurance providers, auditors and regulators.
Organizations also reported greater complexity in their supply chains. Nearly 8 out of 10 respondents ascribed some degree of complexity to their supply chains, with those at the largest organizations much more likely to describe their supply chains as "very" or "extremely" complex.
" third-party ecosystem has become complex, and the open-source software system has been attacked and is an easy target," said one CRA survey respondent. "Without having clear visibility into the remediation process, it poses a big risk."
In other words, a company can easily find itself the victim of "too many cooks in the kitchen" syndrome. But is the problem a surplus of cooks, or a failure to execute effective risk management?
Limited resources and staff
Organizations try to meet a recognized need, but lack the funding, personnel, or tools to make progress. Even though awareness of third-party risk is growing — thanks in large part to the devastating SolarWinds supply-chain attack in 2019 and 2020 — there was general consensus among CRA survey respondents that organizations lack essential resources for managing their business relationships.
Roughly half of all respondents said they lacked qualified staff to implement a third-party management program. Others pointed to an insufficient budget as the primary offender, while still others lamented the absence of an automated technology solution for more effectively managing third-party risks.
Poor visibility
As supply chains grow more complex, it becomes increasingly important for businesses to track all tiers of the supply chain. However, the survey data shows that organizations are largely in the dark when it comes to potential vulnerabilities in the third parties they interface with.
"We don't have visibility into their day-to-day operations, so we don't know how vigilant they are," lamented one respondent.
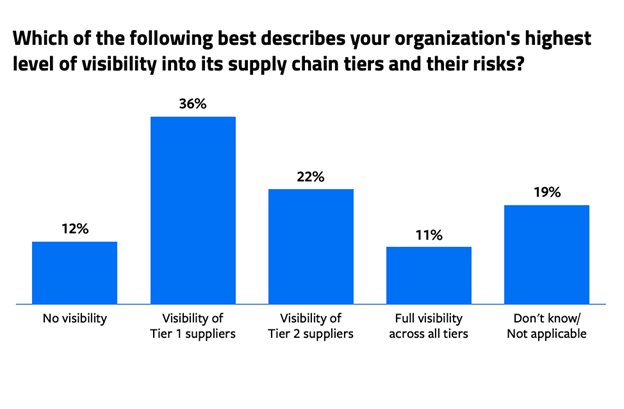
More than a third of security professionals (36%) said their organizations had visibility only into Tier One suppliers — in other words, those that directly provide the final product. Just 22% said they had visibility into Tier Two suppliers, and a meager 11% said they had visibility across all tiers, regardless of supply-chain complexity. Meanwhile, 12% said they had no visibility whatsoever into third-party security operations.
That limited visibility is taking its toll. More than half of those that CRA surveyed said their businesses had suffered an IT security incident — either an attack or a breach — related to a third-party partner in the previous 24 months. Among organizations that were affected, 52% said the source of their attack was via a vulnerability exploited in a software vendor.
"A third-party data processor was compromised which exposed our data to the attackers," said one respondent. "We were notified more than one month after the attack was discovered by the third party."
The average time it took to assess a breach or incident varied widely among respondents. Twenty-one percent said it took several hours, 45% said it took one to six days, 10% said it could take between one and two weeks, 10% said it took longer than two weeks, and 14% didn't know.
Culture clash
Even as most organizations agree on the need for better third-party risk management, it can be difficult to get all parties on the same page with respect to executing reforms.
"We need full buy-in from our third-party partners in mitigating cybersecurity risks," said a respondent. "While most of our partners are aware of the risks and are taking some efforts to mitigate risks, we need to set standards to which we can hold our partners accountable."
Organizations face a variety of obstacles in auditing and managing third parties and coming up with policies to address the risks. Dedicating the funding, time, and qualified staff to this task is daunting, and may seem impossible for many organizations as it often competes with other priorities.
Respondents pointed out that "simply getting the other party to get on board and implement good security can be a formidable challenge."
When a third-party breach did occur, potentially exposing their organizations' sensitive data to attackers, respondents remarked they didn't always receive timely notifications from their vendor or partner, limiting their ability to be proactive in notifying customers and other stakeholders.
How to reduce third-party risks
Even if an organization or its MSSP does everything by the book, third-party risks will remain a considerable threat. However, there are strategies that MSSPs can implement to minimize the impact of third-party weaknesses on their clients and to lessen the chances of successful exploits and attacks.
The good news is that managing third parties effectively is something any MSSP can achieve by instituting the proper policies and procedures. To reduce third-party risk to your client, here are a few things to keep in mind.
1.) Continuously monitor risk
Annual risk assessments of third-party providers used to be good enough, but those days are over. Today's businesses move at the speed of data — and if data assets can be compromised overnight, then so can the business.
Risk assessments give you a snapshot of a vendor's security at a single point in time, not over an extended period. The CRA Business Intelligence report finds that 46% of organizations use annual risk assessments to mitigate risk, whereas just 29% use real-time information, risk metrics and ongoing monitoring of third parties. When possible, organizations should work with vendors to ensure risk can be monitored on an ongoing basis.
2.) Use an automated third-party risk management platform
If the average company has 88 third-party partners, as indicated by the CRA Business Intelligence survey, then there's simply no way to manually track risk across such a diverse network of vendors, manufacturers, distributors, and suppliers.
But automated platforms can provide a single, shareable source of insights, rapidly scan massive data sets to flag potential threats, and generate real-time reporting to give security teams constant visibility of assets used by third parties.
As Dun & Bradstreet noted, "integrating automation into your third-party risk management program may seem daunting, but given the growing complexities in accurately collecting and screening third-party data and the need for deeper due diligence, how else will you mitigate risk while reducing costs?"
Respondents in CRA's survey would agree: Among those who expressed high concerns about managing their third-party risk, 44% cited the lack of an automated solution as a primary obstacle.
3.) Work with vendors that prioritize visibility and cut ties with those that don't
IT security pros surveyed by CRA Business Intelligence repeatedly voiced frustrations about not being able to verify or validate third-party security controls and policies.
"Our top challenge is that we do not have visibility into the vendor's security controls," said one respondent. "Nor do we have control when it comes to auditing third parties — so we have no idea if third parties are in compliance with our regulatory needs."
Organizations should seek out, and MSSPs should assess, vendors that provide clear, consistent communication and transparency regarding security controls, data use, identity, and access management, as well as timely notifications if vulnerabilities are discovered.
4.) Enforce third-party risk management policies and practices
While negotiating contracts with third-parties, organizations should perform their due diligence in ensuring that vendors abide by industry-approved risk management policies. MSSPs can aid greatly in this process. The appropriate policies and requirements include (but are not limited to) NIST's Risk Management Framework, level 2 compliance with Security Trust Assurance and Risk (STAR), the Cybersecurity Maturity Model Certification (CMMC), as well as the Cloud Security Alliance Cloud Controls Matrix (CCM). Additionally, organizations or MSSPs can request that vendors provide a software bill of materials (SBOM) upfront to ensure the integrity of the software being purchased.
5.) Get management on board
According to one infosec professional who responded to CRA's survey, "buy-in from executive management... is a real issue; without it, we can't mitigate third-party risk."
While attention around third-party risk has grown considerably — with 68% of respondents saying it had become a more important priority for their organization in the past year — there is still a vacuum of leadership at the top when it comes to setting the tone for third-party risk management initiatives.
Thirty-eight percent of respondents cited a lack of upper management guidance, and 44% said current budgets did not permit onboarding capabilities that could improve third-party risk management. Consequently, organizations have adopted a reactionary security posture that simply feeds a vicious cycle of "breach-and-respond."
As one respondent put it, "we have so many third-party vendors, and when data breaches show up on CNN, the C-suite and board perk up and expect something to be done proactively to protect our institution from lapses in security from our third-party vendors."
With reliance on third parties only expected to increase in coming years, leadership should put its money where its mouth is by making critical investments in personnel and tools that could help secure growing networks of providers.
Daniel Thomas co-authored this article.




