For what seems like years now, ransomware has captured headlines due to its sensationally disruptive and costly nature. And over these years, phishing has been used to directly deliver ransomware or to use a single intermediary loader, often targeting individual machines for low ransom amounts. However, phishing is now most often a preliminary step in multi-step ransomware operations, rather than a direct delivery mechanism for ransomware itself. The price tags have surged exponentially.

There are two primary factors that have pushed phishing further upstream in the ransomware delivery process.
- Ransomware operations are seemingly more profitable when they focus manual effort on ransoming an entire organization after the initial compromise of an individual member, rather than simply conducting automated attacks against a distributed set of unrelated, individual victims.
- These focused ransomware attacks can be conducted more effectively if the ransomware delivery is segregated from the initial phishing chain. Tools used to establish a pervasive presence and deploy ransomware in the targeted organization’s network may be loaded via the phishing campaign’s malware payload, but only at the command of a human attacker after the automated phishing chain is complete.
Once inside, a threat actor can use any of a large variety of custom and commodity tools to move laterally, escalate privileges, establish persistence and deliver the final ransomware payload. Therefore, an excessive focus on signatures of the ransomware itself is counterproductive. By the time an actual ransomware binary is detectable within a targeted organization’s network, it may be too late to mitigate the impact. Thus, it is more important than ever to catch a ransomware operation at the phishing stage, before it is even identifiable as a ransomware attack.
Ransomware, the Media Headliner
In the context of cyber threats and security responses, ransomware has taken on a life of its own, and has become a major focus of media attention around the world. While a large variety of other threat types exist, many broadly labeled simply as “malware” and “cyberattacks” in media coverage, ransomware is specifically named. Obviously, using ransomware to acquire a ransom is the final objective of any ransomware operation. The process through which threat actors compromise and prepare victim networks for ransomware deployment involves an initial entry vector, as well as a host of other tools, malware and infrastructure.
Phishing is one of the most common entry vectors for ransomware operations. However, the trend of threat actors delivering ransomware directly via a phishing email or via an attached intermediary downloader has diminished. Instead, threat actors now often choose to deliver ransomware using malware originating from a phishing email. For example, BazarBackdoor was used to deliver Ryuk ransomware to healthcare companies in October 2020 and, recently, IcedID was used to deliver OnePercent group ransomware, according to an FBI advisory.
Some recent ransomware related headlines have highlighted software vulnerabilities and account compromises as being key factors in expensive and eye-catching ransomware incidents. Software vulnerabilities, while newsworthy, are generally not recognized as a common ransomware attack vector. Most sources, including the United States Cybersecurity and Infrastructure Security Agency (CISA), state that phishing is one of the leading ransomware infection vectors. Account compromise is the other ransomware infection vector mentioned in recent headlines. This vector can be heavily influenced by credentials stolen via credential phishing or keyloggers, which also originate with phishing. These facts merit increased scrutiny of phishing as a ransomware infection vector.
Focused Ransomware Attacks are More Profitable than Distributed Attacks
In the past, ransomware such as Avaddon was widely distributed via phishing, with little regard for the identity of the recipient. While this tactic proved profitable to an extent, it also limited threat actors. With no idea whether they were infecting an individual, a small business or a large company, threat actors were forced to set a ransom that individuals could be expected to pay. By doing so, threat actors potentially missed out on significantly larger amounts that companies could be expected to pay.
For example, a threat actor might ransom individual employees for $700 each (the average Avaddon ransomware payment at one point). On the other hand, the threat actor could spread laterally and ransom all of the infected machines and shared drives to the company for an average of $170,404. If the threat actor performed additional information gathering (i.e. to determine things like the company size, the company's profit for the last year, and how often the company needs to access the soon-to-be encrypted content), then the threat actor could further tailor the ransom amount to be much higher but still within an "affordable" range.
Shifting from distributed attacks to more focused attacks seems clearly to be more profitable for threat actors, but targeting enterprise environments comes with additional challenges. Enterprise environments are more likely to have security controls in place and more likely to have methods of blocking malicious attachments than a single user with a simple desktop email client. Using large-scale generic campaigns with attached ransomware or attached simple downloaders, as in the past, is generally not an effective way to bypass enterprise security controls. Instead, threat actors often opt to bypass some security controls in two ways. The first is to buy access to enterprise environments that have already been compromised by other malware and then deploy the ransomware. The second is to use methods that can bypass security controls to deliver harder-to-detect payloads, such as Cobalt Strike, which then perform reconnaissance before delivering the ransomware.
Post-Phishing Delivery is More Conducive to Focused Ransomware Attacks
In current operations, ransomware is most likely to be delivered by other malware or tools already placed on the targeted system. Among other benefits to the threat actor (including limiting exposure to researchers and law enforcement personnel interested in ransomware), this delivery tactic helps to bypass initial security controls and collect information to determine whether the compromised machine is part of a potentially profitable ransomware target. Whether this data is provided by a threat actor who has already compromised a computer and is selling access, or by tools used by the threat actor deploying the ransomware, it can allow threat actors to tailor ransom amounts and make more money. The threat actor deploying the ransomware can also perform reconnaissance to target and exfiltrate high value data. This can allow the threat actor to charge ransom for both the encrypted data and the stolen data.
The currently observed methodology used by threat actors consists of several steps:
- Threat actors purchase access to a computer that has already been compromised by previous malware
- Deploy reconnaissance tools to gather information
- Employ lateral movement to establish persistence in multiple connected systems, and then,
- Deploy ransomware
This process takes time. FireEye estimated that, in most ransomware incidents, there were at least three days between an initial infection and the deployment of ransomware. This time can allow a grace period of sorts before ransomware deployment when defenders can detect and take care of the problem. However, that is only the case if the defenders are provided with the tools and intelligence necessary to identify steps preceding a ransomware deployment.
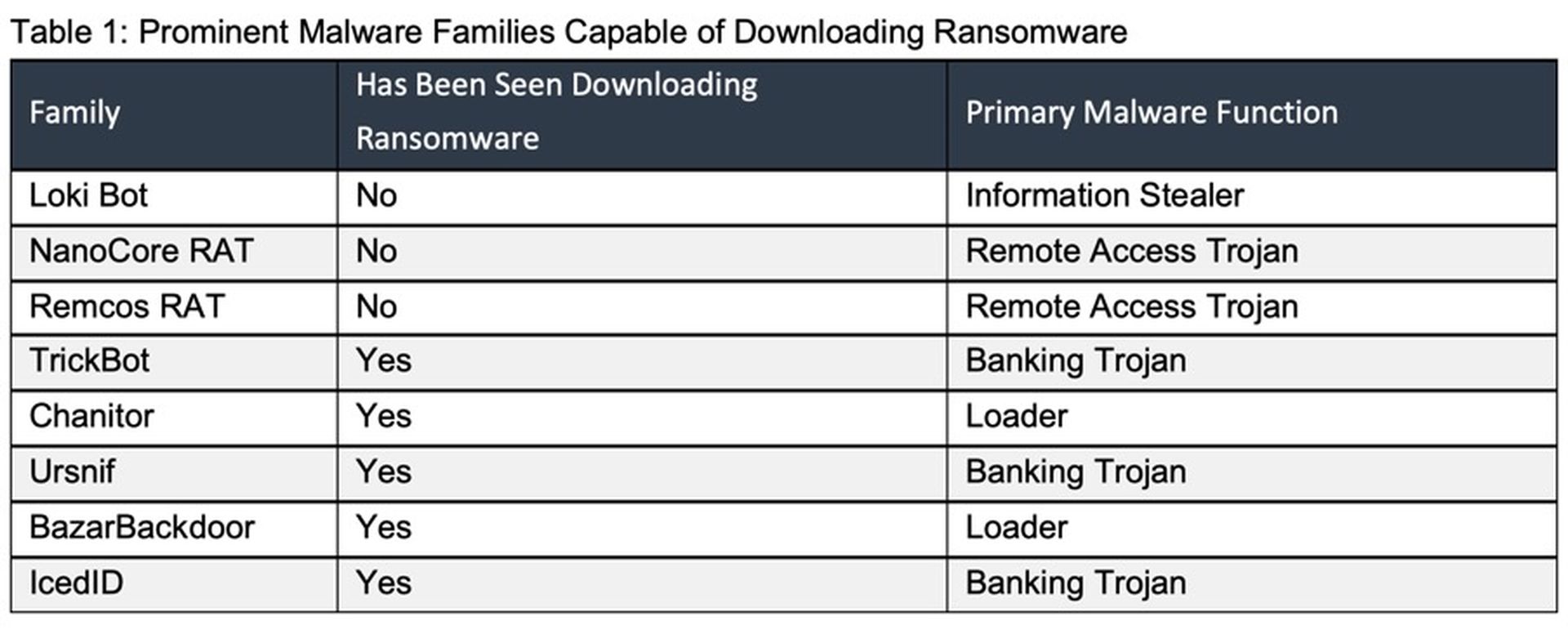
Some of the malware more commonly used to infect computers and sell access to ransomware operators include TrickBot, Dridex, IcedID and BazarBackdoor. These malware families are well known, but advanced enough to bypass some security controls. We consistently see these families reaching user inboxes in environments protected by secure email gateways (SEGs). A number of commonly seen and less sophisticated malware can also deploy additional malware including ransomware. A list of some of the more prominent families that are capable of downloading and deploying additional malware, including ransomware, can be seen in Table 1.
Things That MSPs Should Consider
As ransomware continues to be delivered based on decisions and actions taken by human threat actors, rather than as a default configuration, it becomes increasingly important to look "upstream" at the chain of events that leads to that decision. Treating most malware detections as a potential vector for ransomware may seem excessive, but most advanced malware and remote access trojans (RATs) can deliver additional malware and ransomware. By treating each malware infection as a potential vector, and tracing the steps that led to that infection, you can determine the flaws in your defenses and fix them.
How MSPs Can Help Detect & Prevent Infections: Cofense Protect empowers MSPs to deliver instant phishing threat detection with Computer Vision technology paired with Cofense’s best in class training and simulation – helping your clients be more resilient to attack. Book a demo to see how you can provide advanced phishing protection to keep your clients safe from today's most sophisticated phishing attacks.
Author Max Gannon is malware analyst at Cofense. Read more Cofense guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




