Threat actors are delivering phishing email attacks in greater volumes while rapidly changing their tactics, making them harder for your end-users to identify. It can be hard for MSPs to keep up while countering myths about who is most at risk and who is most susceptible. Let’s examine some of these now.
Myth #1: IT has it covered. Email security is sufficient to stop phishing attacks.
False. While it might be nice to think that native Microsoft email security has this covered, that's not what our testing has shown
When Cofense put Microsoft and other Secure Email Gateways (SEGs) to the test, we found that they are broadly similar to each other in capability. SEGs are relatively good at stopping malicious attachments in emails. Unfortunately, that solves a problem that was important two or three years ago. The question is whether SEGs can cope with modern-day phishing attacks and in particular credential harvesting.
As shown in this chart, SEGs, on average, are missing roughly half of all malicious URLs, which is a preferred way to launch a credential harvesting attack.
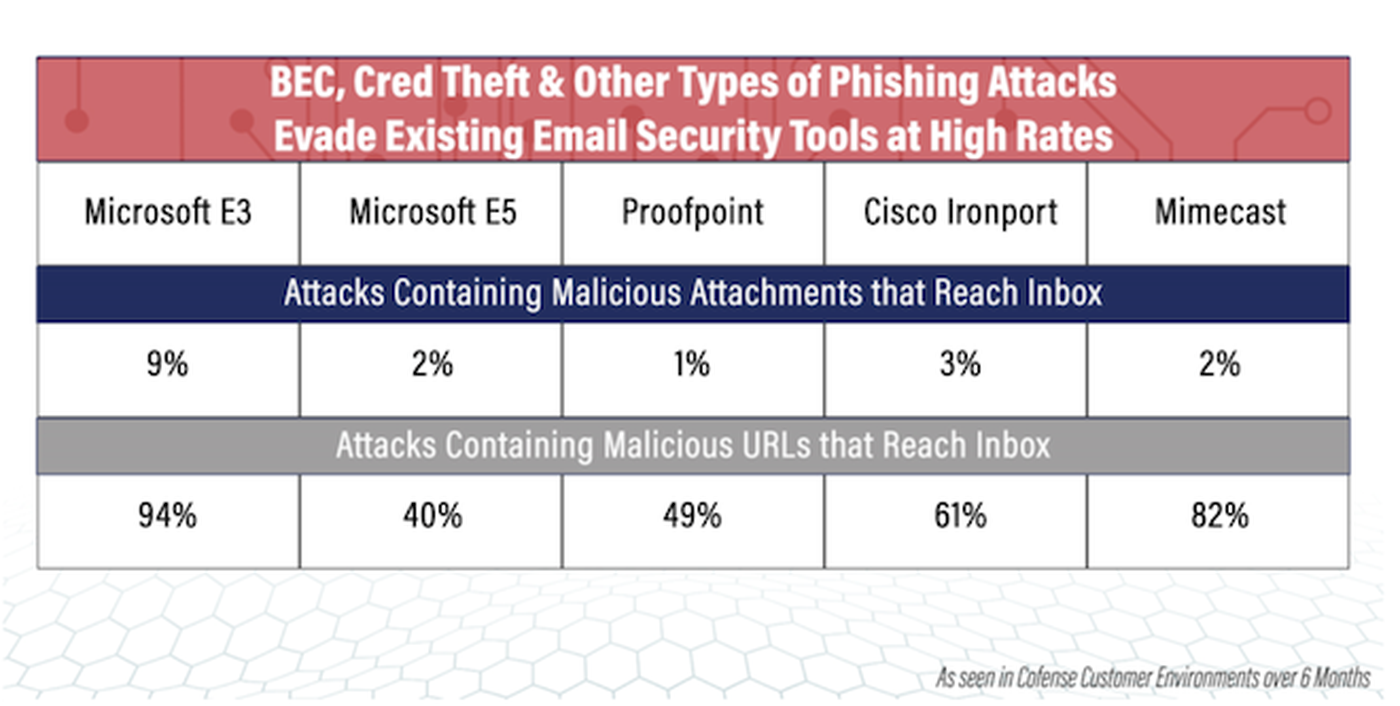
We know nearly 60% of all phish today are designed for credential harvesting, and when SEGs are missing half of all malicious URLs, one thing is certain: There are a lot of credential harvesting emails reaching end users’ inboxes.
Myth #2: Phishing attacks are always easy to spot.
False. There are countless examples of the kinds of credential harvesting attacks consistently slipping past these gateways.
A common one is an offer to share or access a document where the user is presented with a legitimate looking login page for a major brand such as Microsoft Office 365. A trained user can spot a problem with the URL – that it does not match the brand. But many users are busy or distracted. The phish works.
And threat actors may insert a CAPTCHA before a redirect to a login page to help legitimize the attack, but unfortunately a SEG can’t navigate it.
SEGs perform well enough for known threats but they struggle with unknown threats and new or short-lived websites because if a URL isn't on a known deny list, then a SEG will have no reason to not deliver that email.
SEGs also struggle with business email compromise (BEC) attacks. These attacks use regular language containing no flagged keywords a SEG can see. What's needed to detect BEC using technology is the ability to read the content of an email and understand it. Using AI and computer vision gives technology more data points to determine if an email is a phish.
Myth #3: Only less “tech savvy” users fall for phish.
False. This myth is not saying technically-minded employees fall for phish less often than their business colleagues. Instead, this is about the generational aspect of Gen X, Gen Z and millennial users. These groups are sometimes referred to as digital natives.
Digital natives have their own comfort level with what they engage with and post online. The recent Trust Issues survey2 asked how respondents reacted to a suspicious looking email with a link or an attachment. Some 46% percent of Gen Z respondents said they would open the link or attachment, compared to just 1% of Baby Boomers and 4% of Gen X; 29% of Millennials would also take the bait.
Digital natives may be more curious and more apt to interact with odd file types that turn up in environments protected by SEGs. And when joining an organization, they may not be aware of normal business processes. For example, they may receive a request to validate shipping documents, but the message came from the HR department. This is not business as usual, but it happens in phishing attacks.
Myth #4: Attackers don’t target small businesses.
False. Small-medium businesses (SMBs) operating solo and SMBs served by MSPs are just as much at risk as enterprise organizations. The Verizon Data Breach Report3 indicates that 43% of all data breaches involve small and medium-sized businesses, and 61% of all SMBs have reported at least one cyberattack during the previous year. Ransomware directed at MSPs and SMBs can be launched through phishing emails that successfully harvest credentials.
Technology can beat the myths
These myths are understandable considering the technologies available to date.
MSPs can take heart: Modern anti-phishing technology using computer vision and AI that detects, learns and is informed by threat intelligence of what real-world phishing looks like, stops what SEGs can’t.
Contact our team to learn more about Cofense Protect MSP, designed specifically for MSPs. Book a demo to see how you can provide advanced phishing protection to keep your clients safe from today’s most sophisticated phishing attacks.
Related References:
Rich Keith is senior product marketing manager at Cofense. Read more Cofense guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




