Layered security is not a new concept—nor is it one that will blow your socks off. While many organizations understand the importance of cybersecurity, most fail to properly design and implement a robust security stack that is able to stand up to the present day and future threats we’re facing.
Before my role as a Security Engineer at Huntress, I spent about 18 years in the MSP space designing and building secure networks for clients. And now, I speak with countless MSPs and IT teams about evolving and maturing their security stacks. Here’s a common theme I’ve noticed: The reason most of their stacks are lacking is not because they haven’t put thought into them, but because many still have a somewhat dated view of what layered security means.
So what should a modern security stack look like? Keep reading to dive into the critical layers you need and how to get buy-in from decision makers.
The Importance of Layered Security
Five years ago, the industry thought that bundling together a good firewall, some decent antivirus, email filtering and DNS filtering would keep them safe. Realistically, this was considered a solid stack back then. But times are constantly changing, so we must adapt and open our minds to expanding our efforts in security.
Related - Watch our on-demand webinar: Cyber Stack Review: What Should Be In Your Stack?
Attackers have evolved their game and will continue to do so; they crowdsource their efforts, sharing their technology with other bad actors and building more pressure on the defenders of the world. Hackers are getting better at poking holes, finding vulnerabilities and exploiting weak points—in response, we must shift from building a merely prevention-focused stack to building a complete and mature stack.
So you might be asking yourself, “what do I need to do to respond to this reality?” Good question! Luckily, the NIST Cybersecurity Framework can give us some answers.
Understanding the NIST Cybersecurity Framework
The NIST Cybersecurity Framework illustrates how layers of security solutions should work together to minimize the risk of cyberthreats. It’s a straightforward and easy-to-understand model that focuses on five core components: identify, protect, detect, respond and recover.
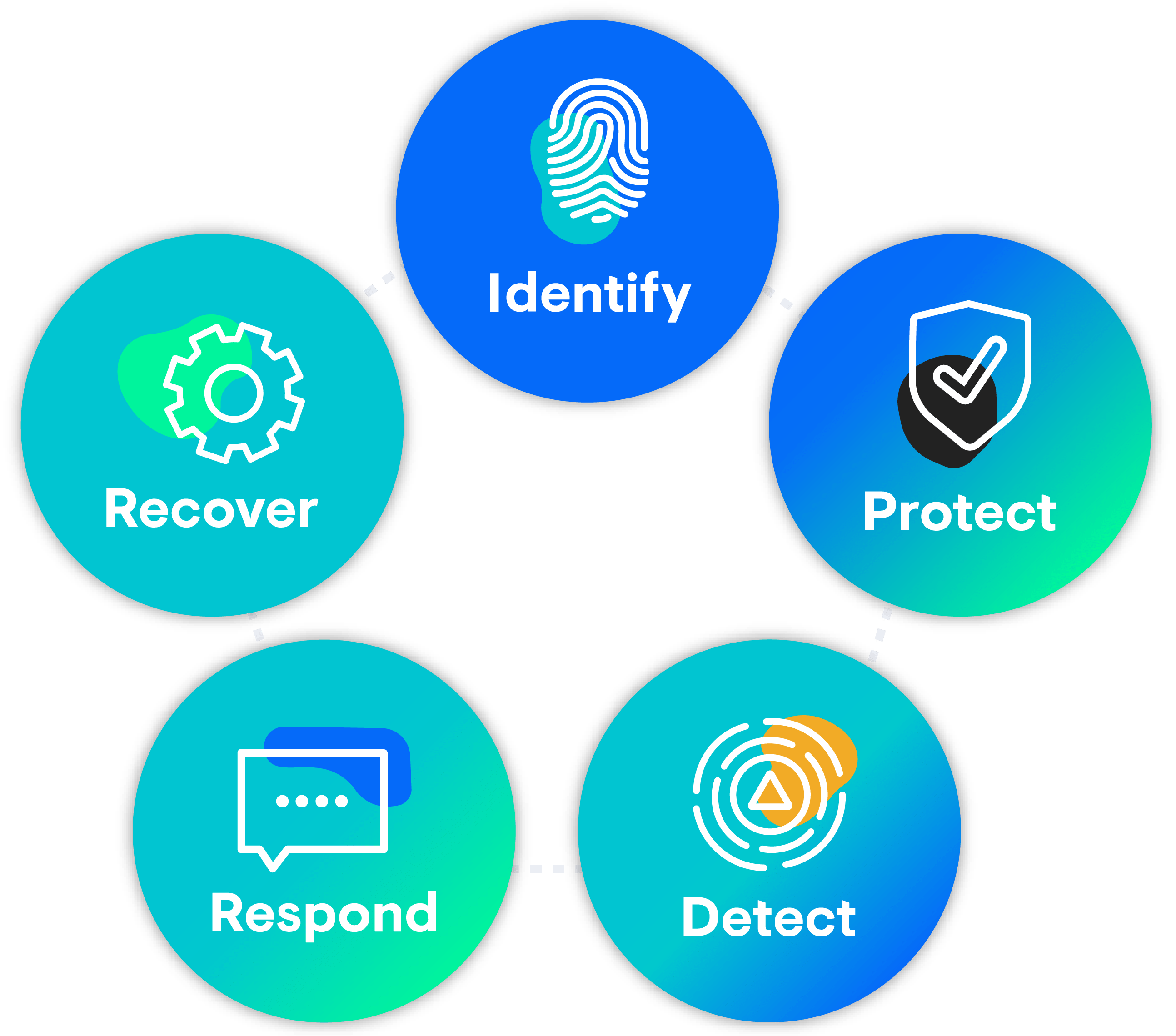
Let’s break down each of these core components.
- Identify entails determining what the critical functions are and what cybersecurity risks could disrupt them. Understanding what you are protecting is the first step!
- Protect supports the ability to limit or contain the impact of a potential cybersecurity event. Examples of these are AV/Firewall/DNS filtering, which is where most security budgets are focused today.
- Detect includes having the relevant measures in place to quickly uncover threats and other risks. This includes continuous monitoring and threat hunting to identify unusual activity and potential attacks.
- Respond focuses on implementing relevant measures to take action against threats that have made it past preventive tools. This includes response planning, threat analysis and mitigation.
- Recovery includes having the tools and strategic plan in place to restore any capabilities or services after a cybersecurity incident.
Hopefully this gives you a better picture of what layers you need coverage in and where you can fill in gaps alongside the existing tools you are already using. As I mentioned earlier, I work with tons of MSPs and IT teams, and (SPOILER ALERT!) most of them have gaps in the detect and respond areas.
Closing the Gap in Detection and Response
Detection and response layers are absolutely critical, yet they’re usually the ones that are most underestimated and under-invested in. One major reason for this is that security has mainly been considered a game of prevention. Traditionally, businesses have opted to build up their outer wall to prevent hackers from getting in. But today’s bad actors often find a way to sneak around, scale or break through that wall.
Companies can invest significant amounts of money on protection-focused tools, but it only takes one believable phishing email to get through. Once attackers are in, preventive tools are no longer effective—and without detection and response capabilities, it’s likely that you may not even know about the intrusion for weeks or months.
This is why those detect and response layers are so important. When hackers sneak in, you need the ability to catch and remove them before they can strike.
But effective detection and response requires genuine security training, experience and knowledge. Solutions like endpoint detection and response (EDR) and network detection and response (NDR) are sought out to fill in the detect and respond gaps, but when not properly managed, these tools can become a river of logs and alerts. And without the right expertise, understanding the real threats buried within all the noise can be a daunting, time-consuming process.
Most IT teams have limited time and resources to spend on managing these tools or hunting hackers down, which is why I see a lot of teams get value from a managed detection and response (MDR) solution that can remove that burden of day-to-day security management.
Recommended Reading: Managed Detection and Response: The Missing Layer in Your Cybersecurity Stack
Furthermore, artificial intelligence and machine learning can help to scale a solution, but they are rarely adequate replacements for actual human experts. There are many living-off-the-land techniques that can trick software and AI because they are built to look legitimate in all the ways a software-only solution cares about. But cybersecurity is a battle between humans—and humans have the contextual awareness and intuition to know when something looks malicious. Plus, humans are also needed in remediation efforts to further investigate threats and put all the pieces together for a complete and swift recovery.
Getting Buy-In for Layered Security
So now that we have established what a mature and modern security stack looks like, how do we get buy-in from decision makers?
As I mentioned, this requires a bit of a shift in mindset and shedding light on the “post-compromise” and the key role that the detect and respond layers play. And while the goal should be to communicate the value of a mature security stack to non-technical or less-technical persons, the truth is that it typically comes down to budgetary constraints. Most companies don’t understand the real cost of a domain-wide ransomware attack unless they’ve dealt with one firsthand. But there are a few thought exercises that you can go through to help decision makers grasp this concept a bit better.
For example, you could run through a tabletop exercise where you simulate an attack and think through how the business would respond.
Don’t be afraid to ask the hard questions and see how they’d respond:
- If we had to completely shut down the network for a week to remediate, how would we operate our business during that time?
- What services would have to remain operational no matter what?
- If we lost sensitive customer information, what process would we follow to investigate the extent and how would we disclose this to our customers?
After these questions, it quickly becomes apparent that it’s better to spend some extra budget up front to prevent this sort of situation rather than wait for it to happen.
You should suggest taking a good look at your existing budget to determine if you’re investing in the right layers and areas. A helpful exercise is to compare your stack to the NIST framework that we covered and the MITRE ATT&CK framework. Are there any gaps? Do you possess overlapping technology? Would it be more sensible to spread budget across tools that cover more layers of these frameworks?
I have also seen many teams struggle with “analysis paralysis” because of the large amount of tools on the market. I mean, just look at how many solutions there are to choose from.
 Source: Momentum Cyber
Source: Momentum Cyber
To combat getting overwhelmed or derailed by the sheer amount of options, seek advice from trusted advisors, or talk to other companies or peer groups about what they are doing with their stacks to find the right stack for your organization. You should also use things like the NIST and ATT&CK frameworks to navigate the path and take action on the areas that matter most.
We no longer live in a world where security can take a back seat or be put on hold. It must become a priority in all organizations—one that you have to be willing to fight for.
If there’s one piece of advice I can leave you with, it’s this: When hackers come hacking, don’t be caught without a proper security stack and plan in place!
Author Shane Rose is a senior security engineer at Huntress. Read more Huntress guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




