As an MSP you may wonder: How good is good enough when it comes to email security? It’s a good question to ask, because over 50% of phishing attacks are sliding past traditional email filtering controls like secure email gateways (SEGs). And stopping under 50% can’t possibly be good enough. Tactics used by threat actors are evolving. A rising number of credential phish and business email compromise (BEC) campaigns are evading traditional email security controls. They’re not utilizing old-school attachment-based malware which are typically more easily identified and stopped.
So what techniques are threat actors using to evade traditional email security protocols? And what are the most common phishing attacks targeting MSPs around the globe? Should MSPs rely on native email security or SEGs alone? Or instead, are there best practices for enhancing your email security?
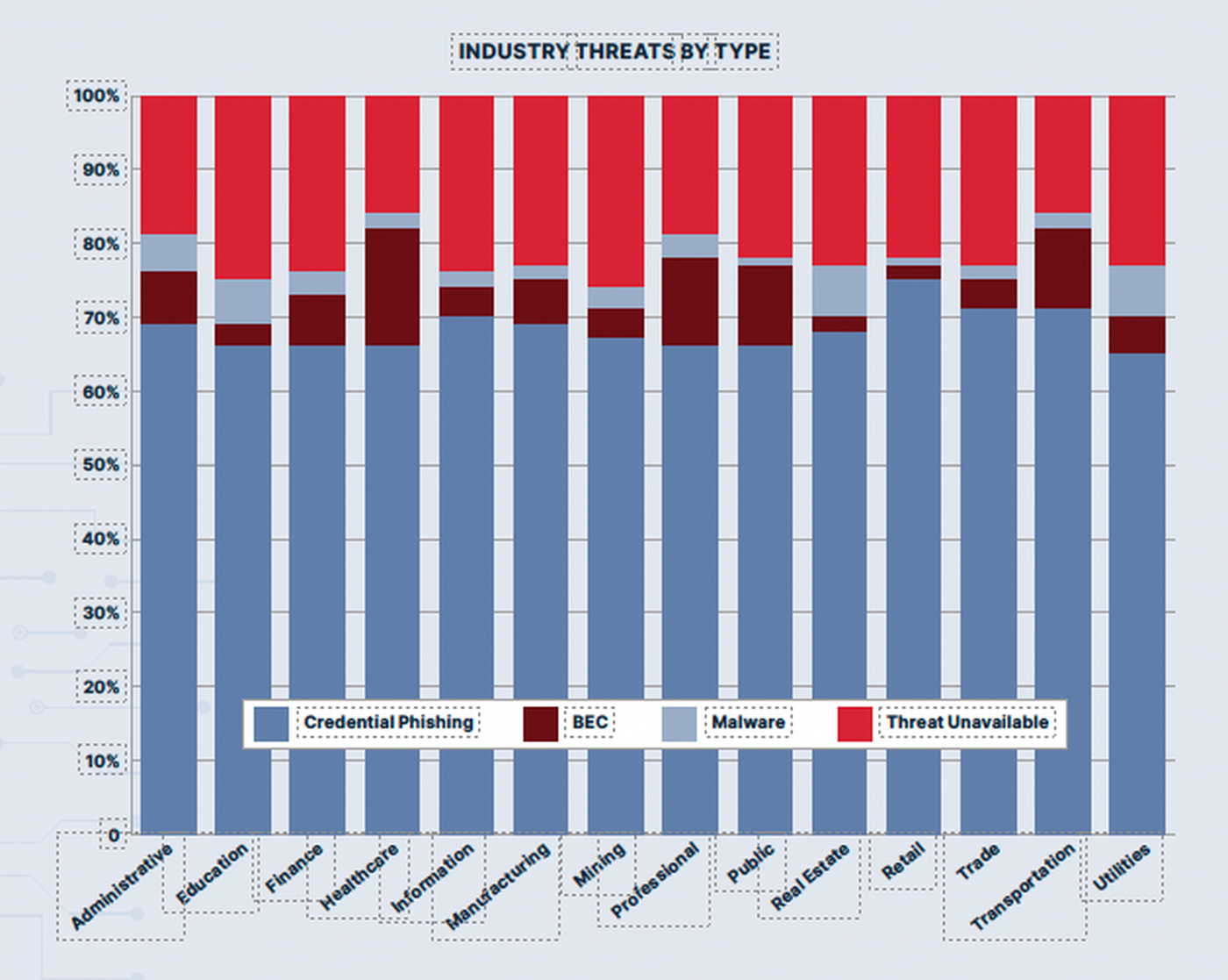
Let’s look at the threat landscape first. In the recently released Cofense Annual State of Phishing Report, credential phishing has increased by 10 percent from 2021, moving up to 67% of all phishing attacks. BEC also showed upward trends as the crafty threat actors are actively increasing their masquerading of common platforms that users will most likely click on. When analyzing reported and detected phishing indicators, the data showed an 80/20 split between URLs versus attachments.
When we talk about attachment-based phishing, sometimes it’s not obvious whether the attachment itself was malicious, or the action that it asked the user to do when it opened the browser was malicious.
For example, if a phishing email contains an HTML attachment, when clicked, it takes the user to a cred phish site. Is this a malicious attachment or do you call this a cred phish? Actually, it could go either way. The site wants the user to enter their credentials. However, because that file may also be embedded with some malware, it could go both ways.
Many of the attachments that we see are HTML or HTM file types that open a web browser that leads into a credential phish. Over the past few years, the number of attachments delivering pure malware continues to decrease.
It’s important to understand why MSPs and other organizations allow this file type in. There are business applications that send legitimate messages using HTML attachments, so it can be very difficult when it comes to isolating them. MSPs can block this filetype by configuring their SEGs, but it might not fit their clients’ businesses.
Most disturbing is how old tricks keep coming back and bypassing SEGs. For example, we have seen attacks using ISO files, which are the old CD-ROM file type. Windows 10 allows these file types to open automatically. These ISO files have bypassed SEGs for months or longer before being patched. When ISO files become blocked, attackers' resort to using floppy disk IMG files. Another relic of the past, IMGs are opened automatically by Windows 10, and again SEGs let them right though.
Added to this, attackers increasingly employ CAPTCHA-protected phishing sites to create a sense of legitimacy. Because of this, rapid detection and response to threats is critical. These links are active in user’s inboxes, and no one wants active links left alive in a phishing email, even if it gets moved to the junk folder.
For more information, you can watch our on-demand webinar, “It's Always A Phish: A Layered Defense is the Best Offense” or download the complete 2022 Annual State of Phishing Report here..
Be sure to read next month’s guest blog where we explain why for the 7th year in the row, business email compromise is number one for cybercrime losses. And how real-time detection is the best first-level protection MSPs have for BEC.
MSPs need a layered email security solution which includes detecting these attacks in real-time and deactivating the malicious links, so they are no longer a threat. Learn more about the real-time phishing detection and user training offered together with Cofense Protect MSP.
Author Rich Keith is senior product marketing manager at Cofense. Read more Cofense guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




